Today we’re coming back to try to solve some cyber mysteries using one of the mostly widely used cybersecurity tools (especially for those working in SOCs as cyber analysts). Splunk is a Security Information and Event Management (SIEM) tool that provides a central location to collect log data from multiple sources within your environment. This data is aggregated and normalized, which can then be queried by an analyst. Splunk is not just for cyber folks; it’s used for data analysis, DevOps, etc. In the two videos below, we’ll walk through the TryHackMe Splunk 2 lab that is part of their Cyber Defense Learning Path.
This lab includes data that was generated in August of 2017 by members of Splunk’s Security Specialist team (BOTSv2). Within the environment there is a good mix of different enterprise devices which means we get access to a great collection of logs. There are a few Windows endpoints instrumented with the Splunk Universal Forwarder and Splunk Stream. The forwarders are configured with best practices for Windows endpoint monitoring, including a full Microsoft Sysmon deployment and best practices for Windows Event logging. The environment also includes a Palo Alto Networks next-generation firewall to capture traffic and provide web proxy services, and Suricata to provide network-based IDS.
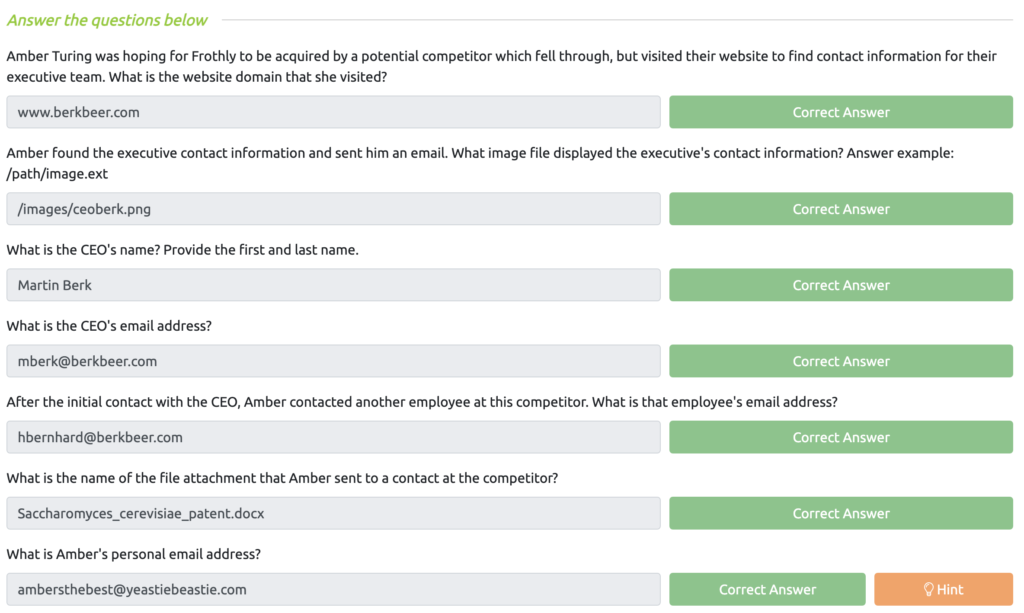
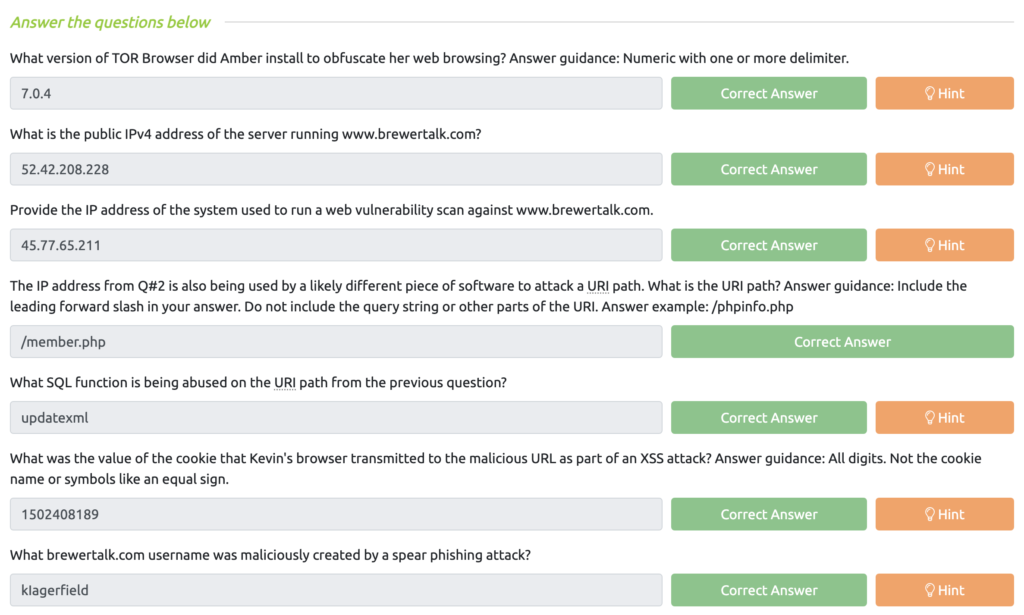
BOTSv2 Questions Series 100 & 200
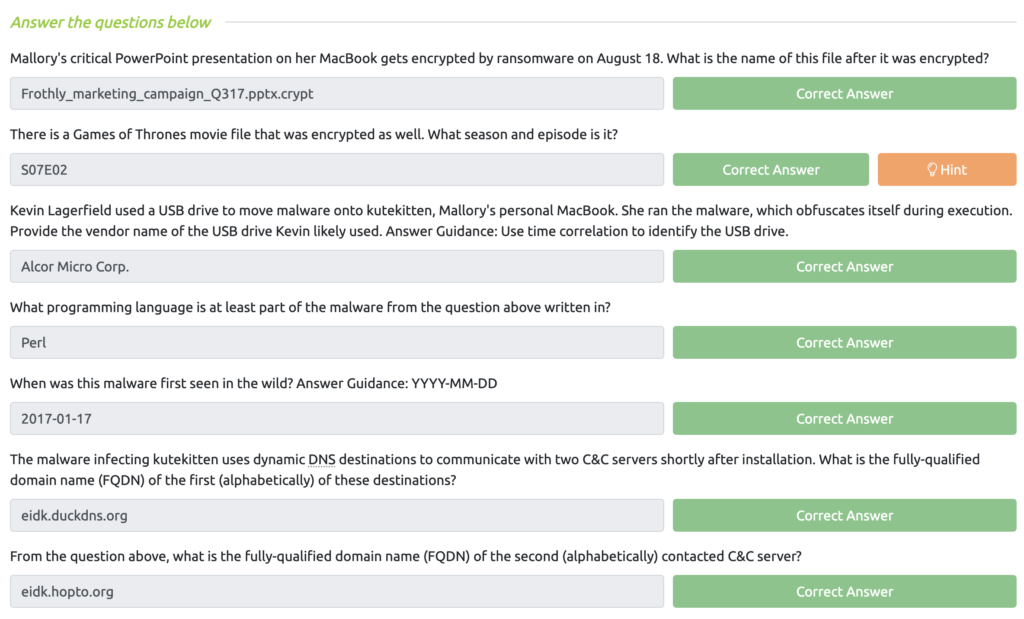
BOTSv2 Questions Series 300 & 400
Network Knowledge Wrap Up
Keep an eye out as I continue to work through other TryHackMe rooms!
And stay up to date on all my Splunk tutorial walkthroughs.