Today we’re talking about one of TryHackMe’s latest room, Wireshark: Traffic Analysis! This room looks at the techniques and key points of traffic analysis with Wireshark and how to detect suspicious activities. This is great information if you’re interested in working in a SOC, on a Blue Team, or even supporting IT operations and need to improve your troubleshooting skills. Since this room covers a lot of in-depth topics, I broke down the tasks into three separate lab walkthrough videos. Be sure to follow along below and subscribe to the CyberInsight YouTube Channel to stay up to date on new lab walkthroughs!
The areas covered by this room include: NMAP scans (TCP connect scans, SYN scans, and UDP scans) ; ARP Poisoning/Spoofing (aka Man In The Middle Attacks); detecting hosts via Kerberos, Netbios, and DHCP; identifying tunneled traffic in DNS and ICMP communication; analyzing FTP traffic; analyzing HTTP and HTTPS traffic including detecting Log4j and suspicious user agents; and how to decode HTTPS traffic. In the last video, stick around for some extra bonus topics!!!
Below I’m going to share with you my answers when going through the knowledge checks in the different tasks in the room. Definitely try to work through the problems as much as you can. Make sure to follow along in the video so you understand what you need to do to get the answers below.
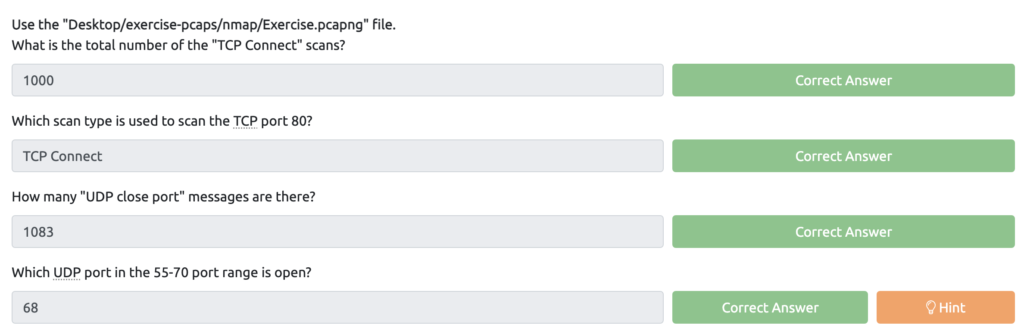
Wireshark: Traffic Analysis Task 2 – Nmap Scans
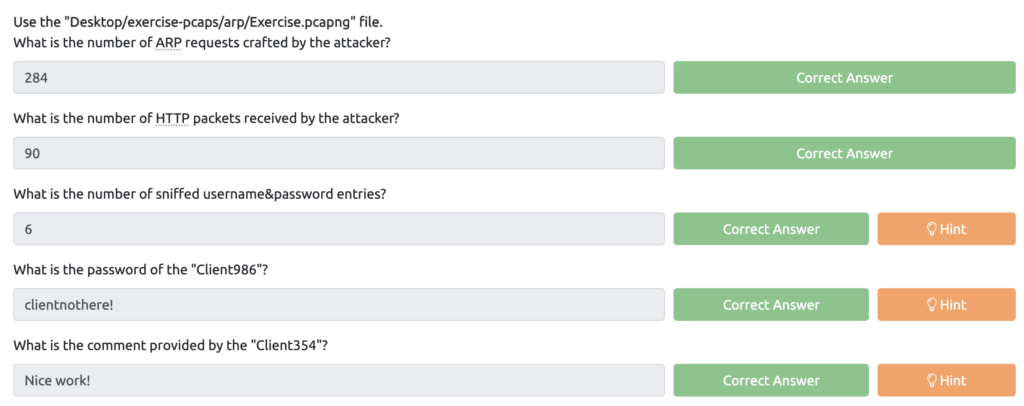
Wireshark: Traffic Analysis Task 3 – ARP Poisoning & Man In The Middle!
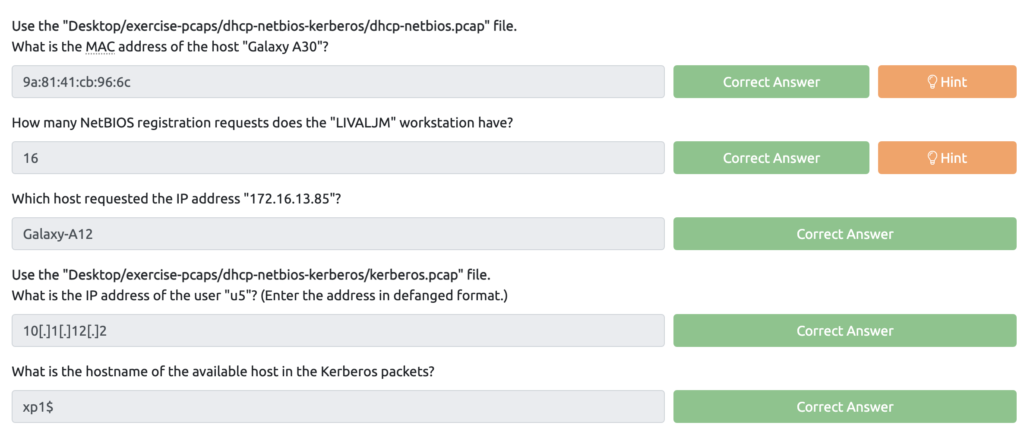
Wireshark: Traffic Analysis Task 4 – Identifying Hosts: DHCP, NetBIOS and Kerberos
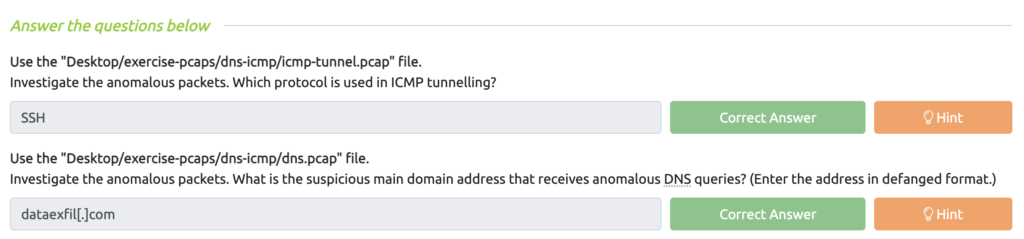
Wireshark: Traffic Analysis Task 5 – Tunneling Traffic: DNS and ICMP
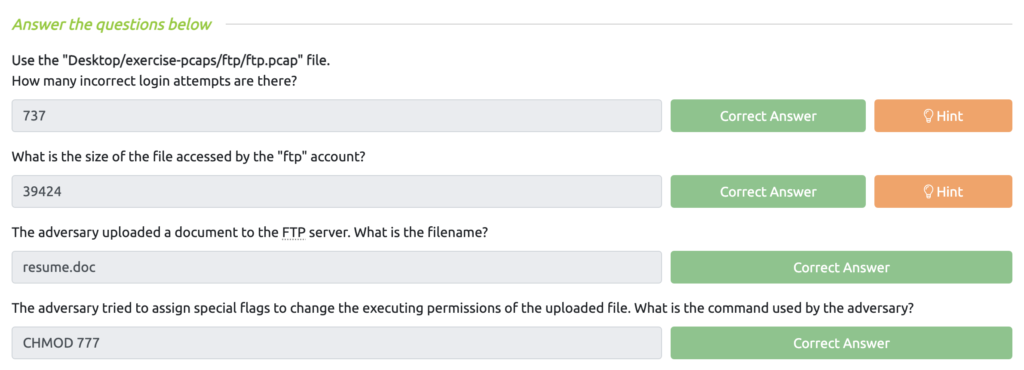
Wireshark: Traffic Analysis Task 6 – Cleartext Protocol Analysis: FTP
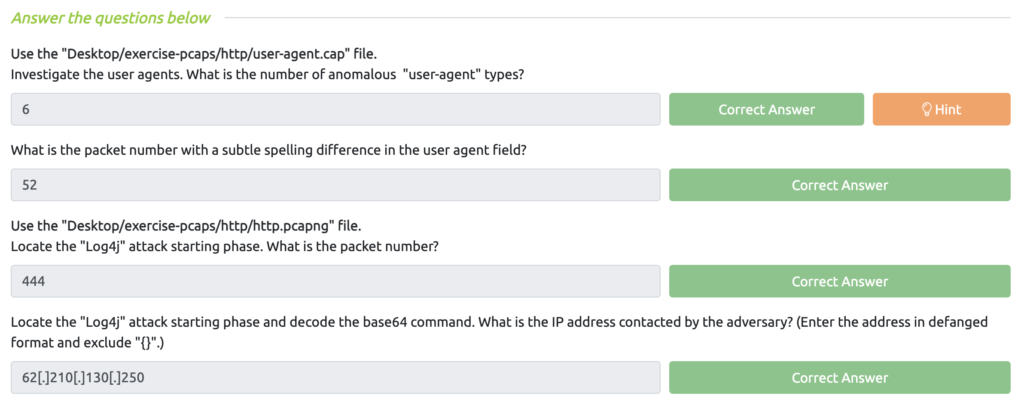
Wireshark: Traffic Analysis Task 7 – Cleartext Protocol Analysis: HTTP
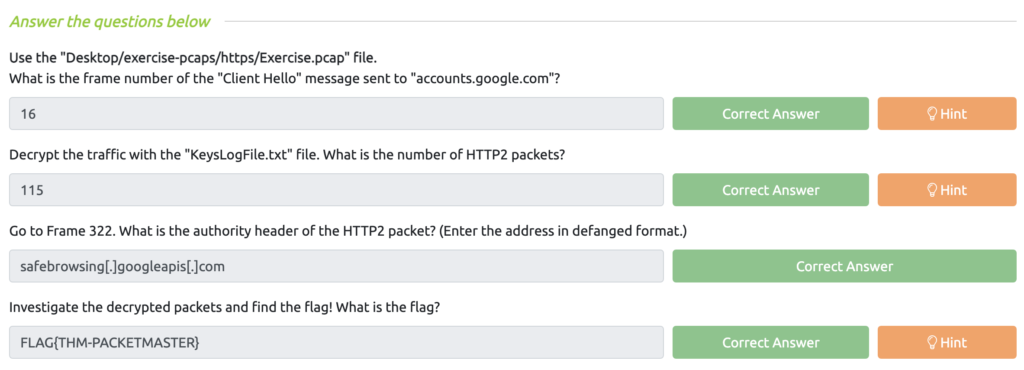
Wireshark: Traffic Analysis Task 8 – Encrypted Protocol Analysis: Decrypting HTTPS
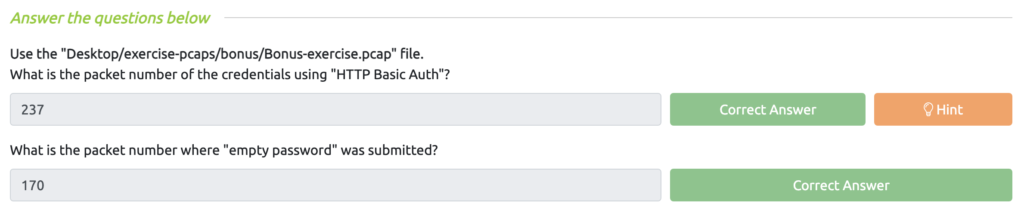
Wireshark: Traffic Analysis Task 9 – Bonus: Hunt Cleartext Credentials!
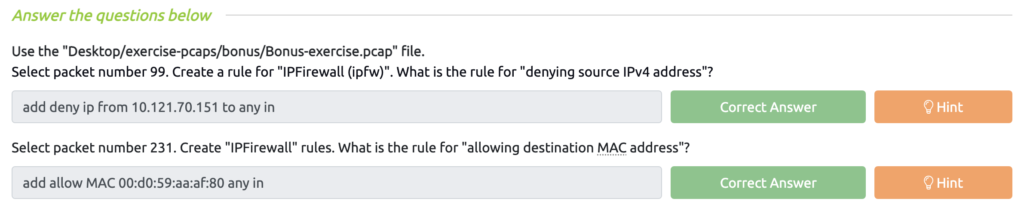
Wireshark: Traffic Analysis Task 10 – Bonus: Actionable Results!
Network Knowledge Wrap Up
Keep an eye out as I continue to work through other TryHackMe rooms!
TryHackMe Wireshark: Traffic Analysis room