Today we’re covering TryHackMe’s Sysmon room. Sysmon, is a tool used to log events that aren’t standardly logged on Windows. It’s commonly used by enterprises as part of their security monitoring and logging solutions, and if you aren’t using it, you should be! In this lab we’re going to be talking about how to install, configure, and optimize it. We’ll then be looking at how to detect ransomware, persistence, Mimikatz, Metasploit, and Command and Control (C2) beacons. Be sure to follow along in the video below!
In going through the configuration options, I there are two prominent configurations files that can be used as a great jumping off point for folks wanting to deploy sysmon. One is by SwiftOnSecurity and the other is by OlafHartong.
Below I’m going to share with you my answers when going through the knowledge checks in the different tasks in the room. Definitely try to work through the problems as much as you can. In this particular room, there are a few tasks that don’t require you to answer any questions, so those tasks are omitted from the screenshots below. Make sure to follow along in the video so you understand what you need to do to get the answers below. This particular room, most of the questions require you to figure out answers based off using tools/commands covered in the lesson.
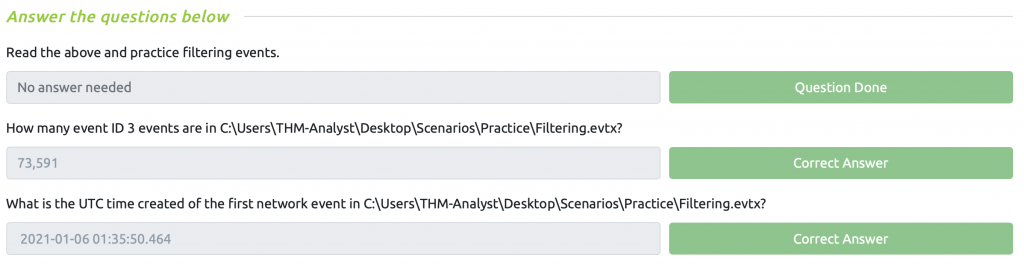
Sysmon Task 4 – Cutting out the Noise
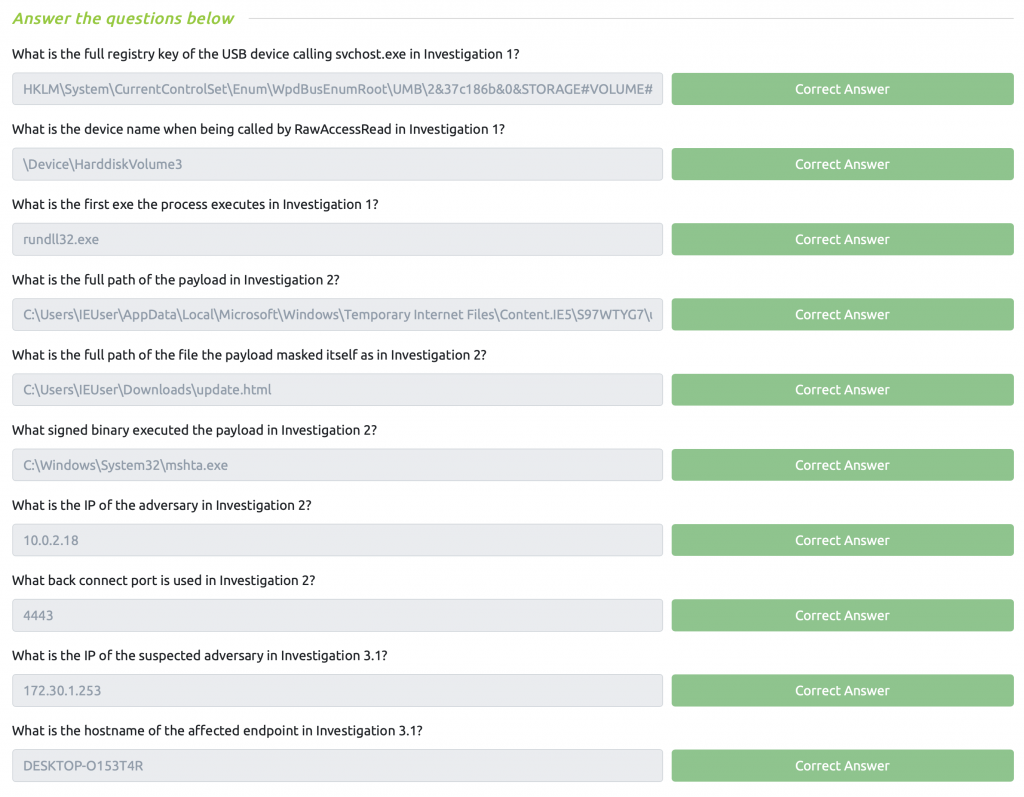
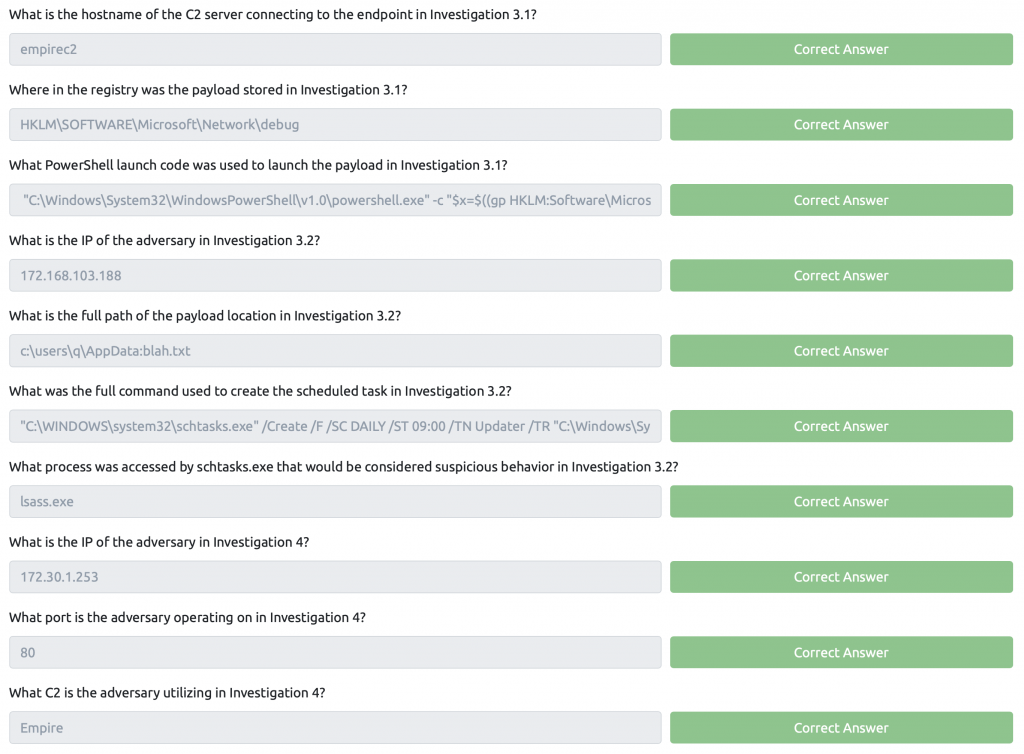
Sysmon Task 10 – Practical Investigations
Network Knowledge Wrap Up
Keep an eye out as I continue to work through other TryHackMe rooms!
Here is the CompTIA Pentest+ training book bundle I used to pass my PenTest+. (Affiliate Link)
TryHackMe Sysmon room