This blog introduces a useful framework for new engineers trying to figure out how to securely build out IT environments. For new people, it’s kind of hard to have a good idea of what are some best practices from a security perspective. The following is a breakdown of a guide that is used by folks in the federal government, but it is something that many people who aren’t necessarily in those environments, might not even be aware exists!
Many new engineers don’t really have a good starting point for where to even go to look when it comes to building out secure information systems. There are many different frameworks out there that can kind of provide some level of guidance. So, let’s take a look at the NIST 800-53 framework and specifically look at the different control families that are somewhat more aligned with technical controls. For those who aren’t familiar with NIST 800-53, also known as the security controls traceability matrix (SCTM), it is a document that the federal government utilizes to ensure compliance of new systems that are becoming active and going an accreditation process.
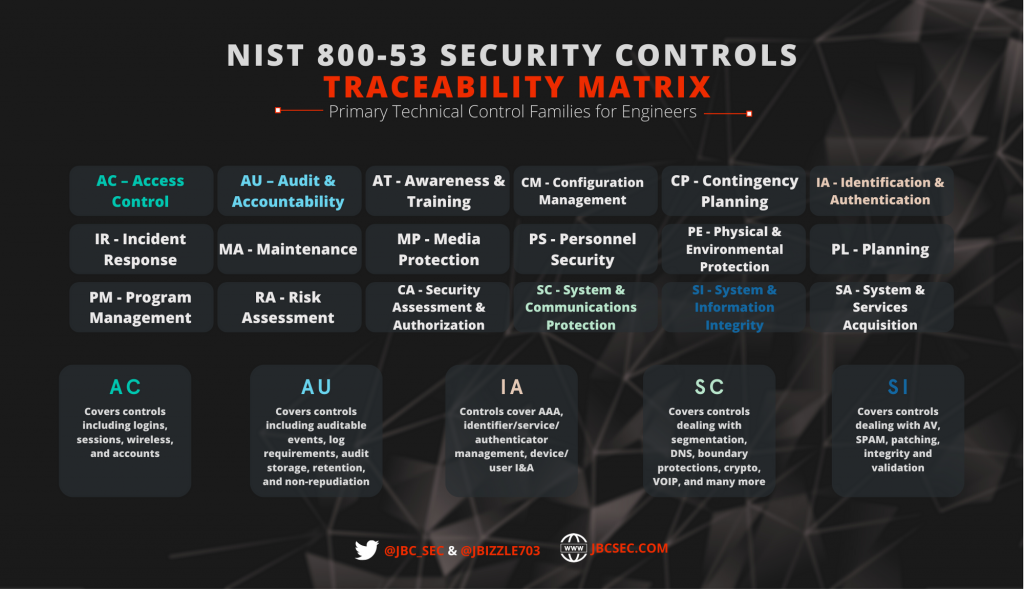
The NIST 800-53 is made up of 18 different control families and those range anywhere from things dealing with access control, user training, maintenance, disaster recovery, physical protections for the IT environment, and each of those in some ways have a varying level of applicability to the things that engineers are working on. In the above diagram, I highlighted the ones that really have a large amount of security configurations in them, ones that give some guidance as far as how you would actually want to build out the environment. Now, all of these control families have policies and procedures that are written to go along with them but, when it comes to actual implementation of specific technologies and configurations, they vary quite a bit. So I we’re really focusing on the ones that have a heavy amount of configurations and technologies that engineers would be looking at and that they would implement in their environments.
The five that I mainly focused on are Access Control, Auditing and Accountability, Identification and Authentication, Systems and Communication Protection, and System and Information Integrity. I’m going to put a link for the NIST 800- 53 documentation right here. Take a look at the different control families and other controls within those control families. Once you really dig into that, you’ll notice that each control family has a whole list of different controls and configurations that you would need to implement in order to be compliant from a federal government accreditation perspective.
Today, we’re not talking about using this specifically to get any type of accreditation on any system. Instead, we’re using it as a way to facilitate a conversation for folks who might not be aware of a good starting point when it comes to actually building out IT systems. The Access Control family focuses mainly on configurations for logins, so things like who is logging in, failed logins, limiting shared accounts. It also covers things dealing with sessions, such as session timeouts and how many sessions should be allowed going to certain types of devices. It also covers wireless configurations and various types of account configurations.
Next is the AU control and that deals with audit and accountability. Think of this as a control that helps you define what you should be logging, how often you should be logging, where you should be logging it, and the types of audit protection mechanisms. Remember, even though this covers a list of the types of events that they would want you to be auditing, it is not the be-all end all. There’s always going to be unique types of event logging that you should be doing within your organization that’s not covered by a framework or guidance document. Likewise, you could look at the list of events that they want you to be auditing and some of them might not be needed depending upon your environment, the tools you have in place, or the amount of storage that you have to be able to handle all those logs. However, it is a good starting place!
The third group is the Identification and Authentication (IA) control family and this deals with everything that’s related to user accounts and authorization. Remember AAA is stuff dealing with authentication, authorization, and accounting. So, here we’re talking about anything that deals with authenticator, identifier, or service management. This control family is the oversight for management of passwords, usernames, multi-factor authentication, and other things of that nature.
The fourth group happens to be my favorite group: the System and Communications Protection (SC) control family. This family covers things such as network and service isolation and segmentation, DNS, boundary protection, firewalls, IDP, and cryptographic protections. Other technology such as Voice over IP (VoIP) fall into this control family. It’s one of the more technical ones (which is why it’s my favorite), and covers a large amount of systems and protections that you would need to implement in your environment.
Finally the last group is the System and Information Integrity (SI) control family. This deals primarily with flaw remediation, so things like patching and patch management. It also covers antivirus protection, spam protection, and other types of integrity and validation controls.
The Wrap Up
I think this is a good starting point for folks who want to dig more into these specific controls and topics. I’m going to make a few more videos/blogs, deep diving into each of these control families. Also, we’ll start to cover more specific controls that might help you build out a more secure environment!